Get help with Linux, Automation, Cybersecurity and more. AGIX staff have the know-how and experience to help your organisation with best-practices, current technology in various Cloud environments including Amazon AWS. Our technicians support Ubuntu, Redhat, Databases, Firewalls, Ansible and Terraform, Storage and more.
This page shows examples of our work that AGIX shares freely with you. For a fully supported compute environment, contact our team to find out how we can help your organization move forward in the right way.
Contact our friendly team to get started.
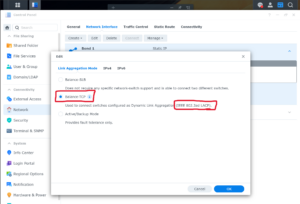
This article shows how to configure the Synology NAS and UniFi switch to use multiple ethernet connections to increase speed. In this article, we’re using two Ethernet cables, but more is possible too. The hardware used in this article are: Synology NAS DS720+ running DSM 7.2.1-69057 Update 5 UniFi US-8-60W
Read more
This article demonstrates how to install and configure the Zabbix Agent2. Our Zabbix server is already up and running, but the host (that we’re about to add) isn’t listed in Zabbix yet. On the Zabbix server: Log into the Zabbix web portal => Data collection => Hosts => Create host
Read more
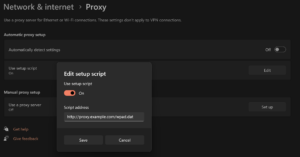
This article demonstrates how to install and configure a Squid proxy along with a WPAD to assist with client configuration. Paths to configuration files may vary between system types. Both http and https will work through this proxy. We’re going to install the Squid proxy and Apache web server on
Read more
This article demonstrates how to allow access to specific directories while denying access to all other directories. We’re using Ubuntu 22.04 and Apache 2.4.58. We’ve got two directories that we want to explicitly allow access to: “east” and “west”. All other directories (existing or not) are denied with a “403”
Read more
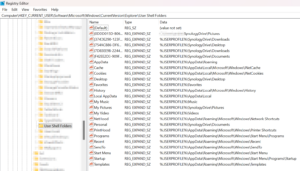
Windows likes to store documents and other content in OneDrive. But for those using Synology Drive, the idea of replacing the path from OneDrive to Synology Drive is attractive. This article shows how to set the Synology Drive folders as your defaults for Documents, Downloads, Pictures, Videos, etc. You have
Read more
PostgreSQL allows for a kind of snapshot to be taken before changes are made. Once the changes have been made, the administrator has the option to accept the changes or roll back to the previous state. Test before use. Note that any changes made between the “BEGIN” and the “ROLLBACK”
Read more
If you’ve using the Microsoft “Family Safety” app to put restrictions on kids while they use their Android phones, you may also want to include their computer in the restrictions. If so, you’re in the right place. We’re using a Lenovo Windows 11 computer purchased in 2024. While the computer
Read more
This article explains the structure of a cipher suite. A cipher suite is a description of a combination of cryptographic algorithms that a system supports, expects or proposes. The description includes a means to create and exchange asymmetric keys, the type of symmetric keys to use, and the hashing algorithm
Read more
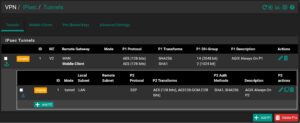
This article demonstrates the settings required on Windows and pfSense to get a Windows Built-In VPN to work between the two. It’s actually pretty easy. This article is more a confirmation of settings than a guide. Make sure you have the firewall rules configured on the pfSense WAN interface. We’re
Read more
This article demonstrates how to extent a LUKS encrypted volume. We’re using Ubuntu 22.04 and the volume is non-root. Although you could probably do the same on the root volume (partition). This is risky and you should not do this without a backup and understanding the likelihood of failure. This
Read more