This article demonstrates how to install and configure the Zabbix Agent2. Our Zabbix server is already up and running, but the host (that we’re about to add) isn’t listed in Zabbix yet. On the Zabbix server: Log into the Zabbix web portal => Data collection => Hosts => Create host
Read moreGet help with Linux, Automation, Cybersecurity and more. AGIX staff have the know-how and experience to help your organisation with best-practices, current technology in various Cloud environments including Amazon AWS. Our technicians support Ubuntu, Redhat, Databases, Firewalls, Ansible and Terraform, Storage and more.
We support Redhat Enterprise Linux, Ubuntu, Mint, Fedora, Debian, CentOS Linux and more.
AGIX is a Redhat and Canonical (Ubuntu) Partner.
This page shows examples of our work that AGIX shares freely with you. For a fully supported compute environment, contact our team to find out how we can help your organization move forward in the right way.
Contact our friendly team to get started.
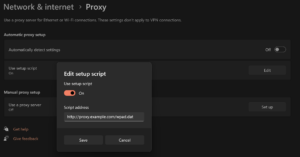
Building a Minimal Web Proxy & WPAD
This article demonstrates how to install and configure a Squid proxy along with a WPAD to assist with client configuration. Paths to configuration files may vary between system types. Both http and https will work through this proxy. We’re going to install the Squid proxy and Apache web server on
Read moreWhitelisting Directories with Apache
This article demonstrates how to allow access to specific directories while denying access to all other directories. We’re using Ubuntu 22.04 and Apache 2.4.58. We’ve got two directories that we want to explicitly allow access to: “east” and “west”. All other directories (existing or not) are denied with a “403”
Read moreA Quick Understanding of Cipher Suites
This article explains the structure of a cipher suite. A cipher suite is a description of a combination of cryptographic algorithms that a system supports, expects or proposes. The description includes a means to create and exchange asymmetric keys, the type of symmetric keys to use, and the hashing algorithm
Read moreExpand a LUKS Encrypted Volume
This article demonstrates how to extent a LUKS encrypted volume. We’re using Ubuntu 22.04 and the volume is non-root. Although you could probably do the same on the root volume (partition). This is risky and you should not do this without a backup and understanding the likelihood of failure. This
Read more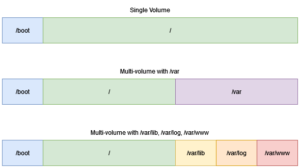
A Single Volume Versus Multi-Volume Disk Layout On Linux
This article discussed the differences between a single volume (/boot + /) and a multi-volume (/boot + / + /var + …). Or to put it another way, one volume with everything on it versus several volumes for different directories. There’s plenty of arguments for both sides. We’re basing our
Read moreDeleting the Bash History
There are times when you want to clear out the Bash history and make a clean start. Or perhaps you want to remove a single or select item/s from the Bash history. Both of these scenarios are accomplished as described below – although we’ll focus on clearing out the entire
Read moreCreating and Mounting Luks on boot
This article explains how to mount a Luks volume (encrypted) on boot. You’ll be asked for a password. There’s plenty of articles explaining how to do this with a crypt-key available, so I need not repeat their work. Here’s our scenario. Remember, this process is destructive. Follow this only in
Read moreCreating New Users & Placing SSH Keys on Ubuntu and CentOS/Redhat
This is a simple reminder to those creating user accounts on Linux systems with the expectation that the intended user will be able to log in using their SSH keys. There’s also instructions on adding them to the “sudoers” groups. Ubuntu & CentOS/Redhat Create the user and place their SSH
Read more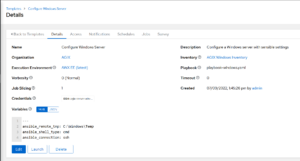
Ansible AWX Targeting Windows via SSH – The details you might have missed
This article highlights some important details for those working with Ansible AWX. Specifically, when the target system/s are Windows based. The two options to target a Windows host is WinRM and SSH. SSH is easier. It just requires the OpenSSH Server “feature” to be installed which is a simple process.
Read more