Get help with Linux, Automation, Cybersecurity and more. AGIX staff have the know-how and experience to help your organisation with best-practices, current technology in various Cloud environments including Amazon AWS. Our technicians support Ubuntu, Redhat, Databases, Firewalls, Ansible and Terraform, Storage and more.
This page shows examples of our work that AGIX shares freely with you. For a fully supported compute environment, contact our team to find out how we can help your organization move forward in the right way.
Contact our friendly team to get started.
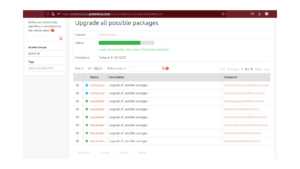
In recent times, we’ve been experimenting with Landscape from Canonical. This article describes our experience. While I don’t claim to be an expert (or even a long time user) of Landscape, I have spent time to test and deploy it. While I hope I have missed a few key points,
Read more
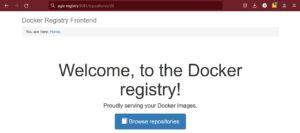
This article walks through the process of creating a self-hosted Docker Registry. We’re using Ubuntu but given that Docker is basically cross-platform (in a way), this should work on any Linux distribution. You can host your Docker Registry on any host you like. When I refer to you “Docker Registry
Read more
This article walks us through the process of installing and configuring two Postgres servers for stream replication. “Stream” replication allows us to replicate all databases from the master to the/a slave. There’s another kind of replication called “Logical” replication, that will replicate “individual” databases on the master to the slave.
Read more
This article describes the fastest way I know to upgrade a WordPress site. A little background: I recently had a WordPress site that was error’ing when attempting to administer it. There were missing functions, etc. I decided to simply upgrade the WordPress code-base to the latest and solve the problem
Read more
In this article, we’re modifying an existing OpenVPN site-to-site (peer to peer) VPN. We’re aware of the change that will come into effect soon that OpenVPN will no longer support shared keys for site-to-site VPNs. We’re going to modify an existing VPN to use SSL rather than the shared key
Read more
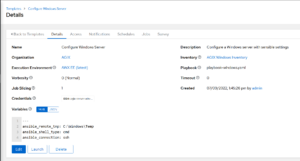
This article highlights some important details for those working with Ansible AWX. Specifically, when the target system/s are Windows based. The two options to target a Windows host is WinRM and SSH. SSH is easier. It just requires the OpenSSH Server “feature” to be installed which is a simple process.
Read more
This article demonstrates how to join/bind a Redhat/CentOS or Ubuntu Linux system to an Active Directory domain, and auto creating user’s home directories as they login for the first time. Prepare and Join Linux to a Windows Domain Set the Hostname Check the hostname. This is the name that will
Read more
NX is an alternative to VNC allowing management of a remote system. NX is opensource (there’s a commercial version), supports encryption, and can be installed on Linux, Windows, and MacOS. This tutorial shows how to install NX on a Ubuntu server, and NX on a Windows 11 client. We’ll then
Read more
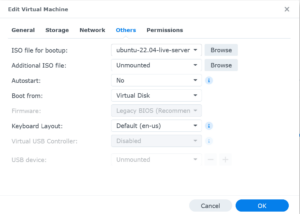
This article shows the correct settings to use for running a Ubuntu Linux virtual machine on the Synology NAS. The default settings wont work, but with a few adjustments, you can easily run Ubuntu Linux virtualization on a Synology NAS. The virtual machine manager settings windows should look similar to
Read more
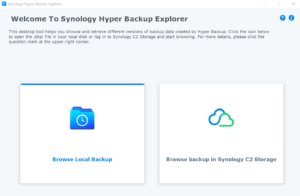
The Synology Hyper Backup software is great for creating scheduled backup tasks, but there is basically no guide or documentation on how to do a DR test. Essentially, when doing a DR test, we want to know it’s out-of-band and not going to interrupt production system, and can simulate a
Read more