This article demonstrates the settings required on Windows and pfSense to get a Windows Built-In VPN to work between the two. It’s actually pretty easy. This article is more a confirmation of settings than a guide.
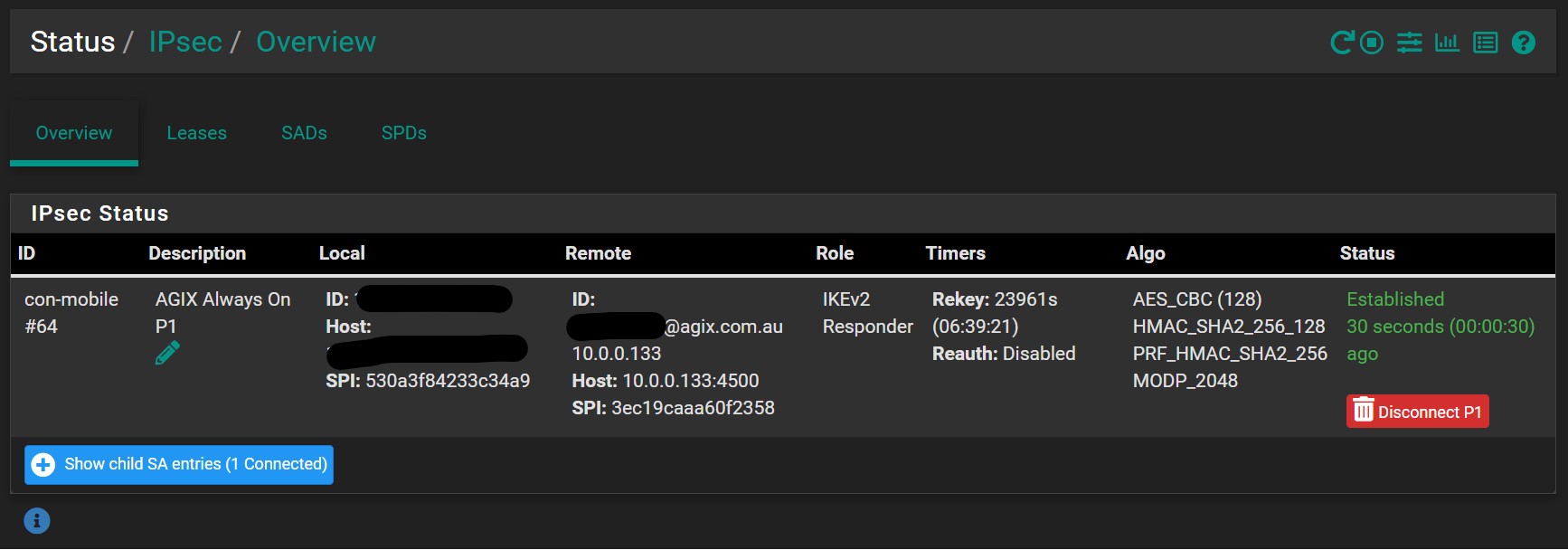
Make sure you have the firewall rules configured on the pfSense WAN interface. We’re allowed for weaker encryption options, but Windows 11 selected the stronger cipher suite.
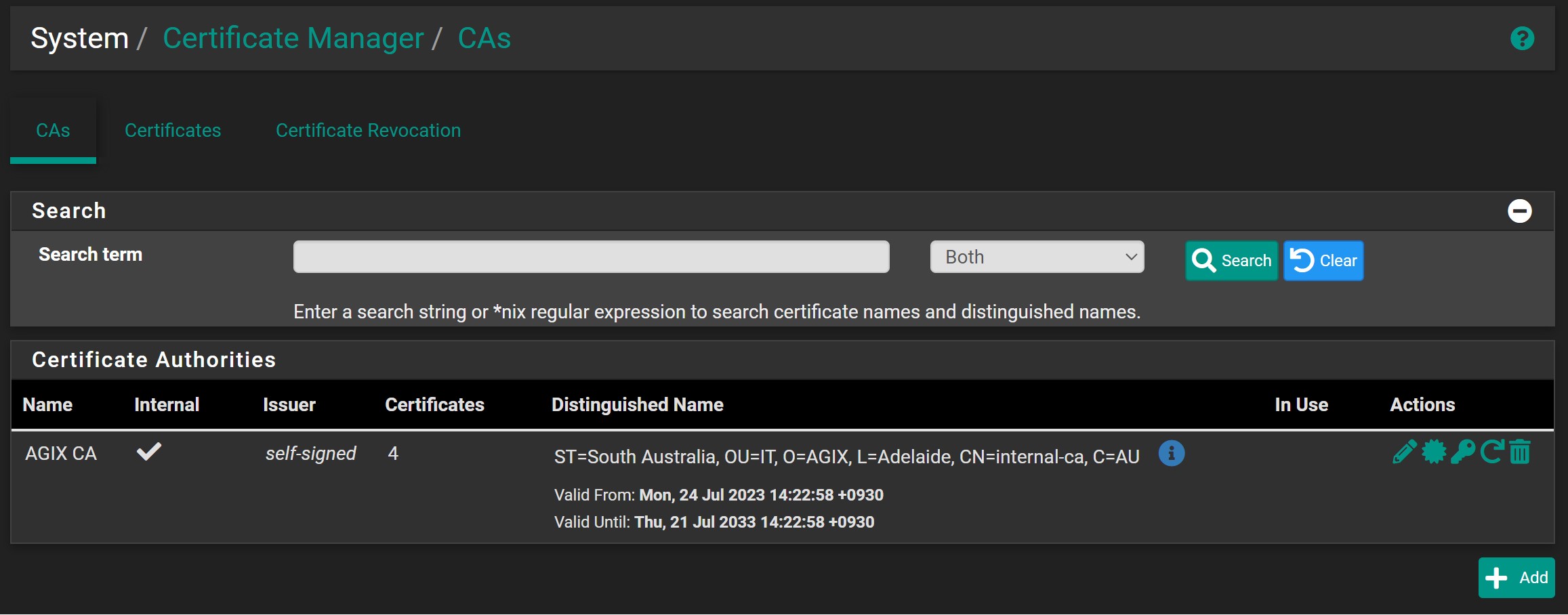
We’ll start with the pfSense Certificates. We need a CA certificate which will be used to create a “server” certificate that IPSec will use. You probably already have a CA certificate. The “server” certificate needs to have the right “CN” and “ALT” name. In this example, we’re using “vpn.agix.com.au”:
The CA:
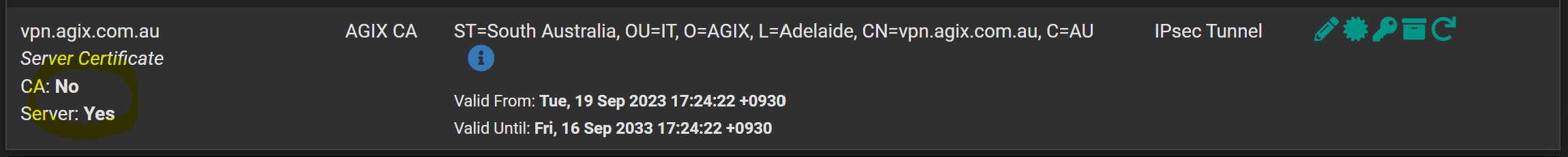
The “server” certificate – notice that it’s “Server: Yes”. The common name and ALT name is “vpn.agix.com.au”. This is important to get right. It represents the address that the Windows computer will look at for the VPN end point on the pfSense:
Now the IPSec overview:
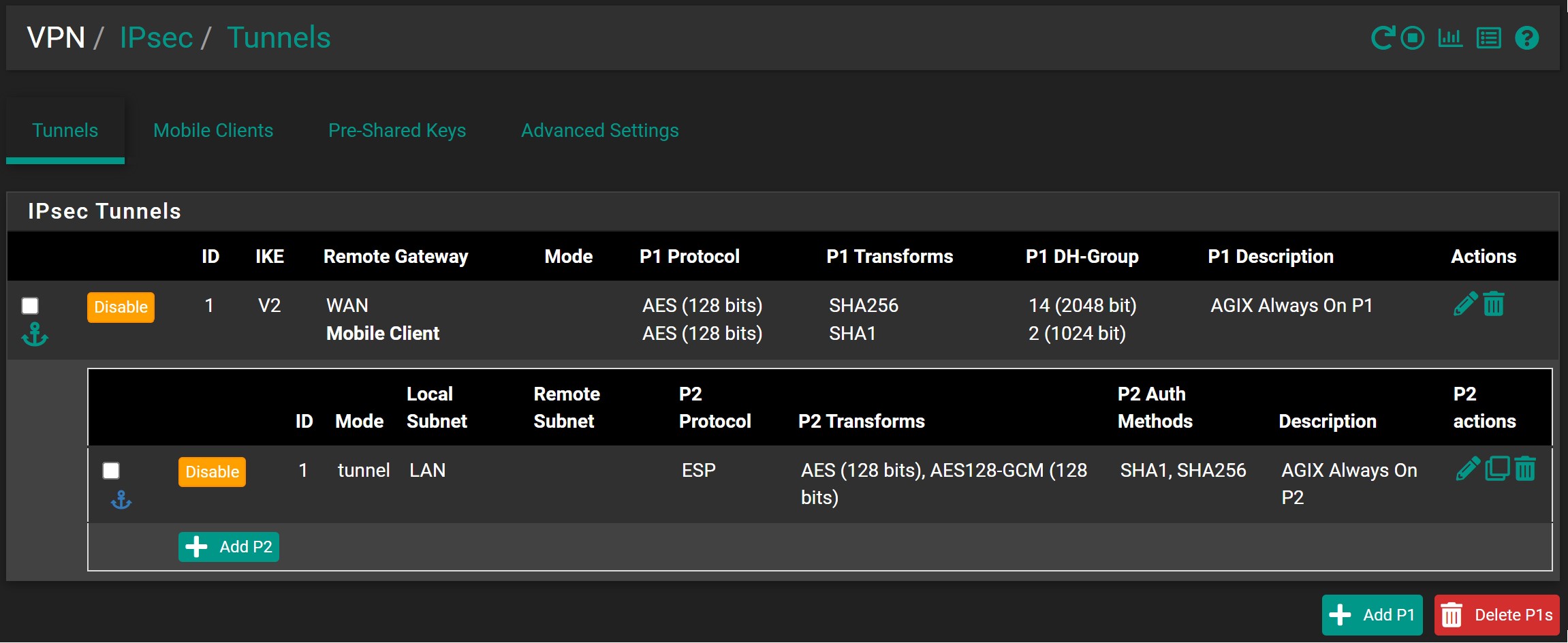
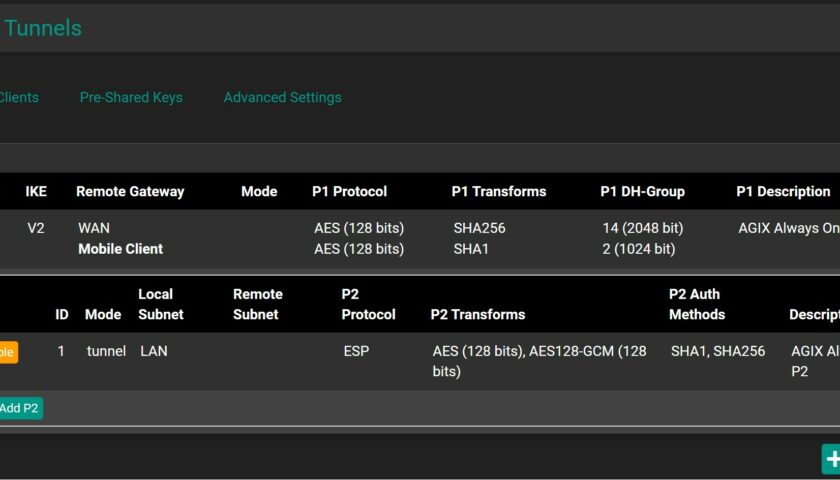
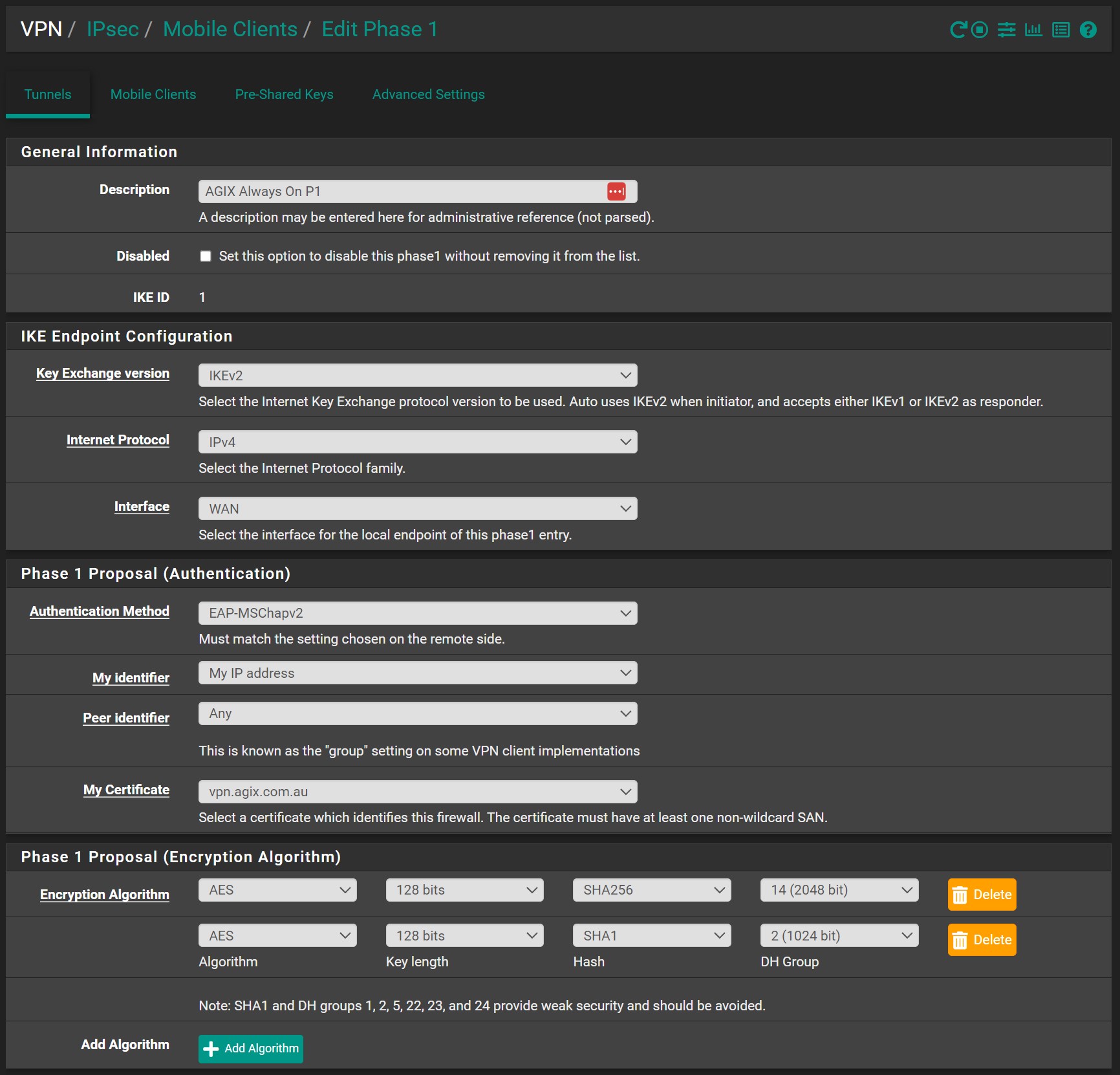
Confirm the IPSec Phase 1 (P1). Notice the certificate is the one we created earlier. For this example, the certificate is “vpn.agix.com.au”:
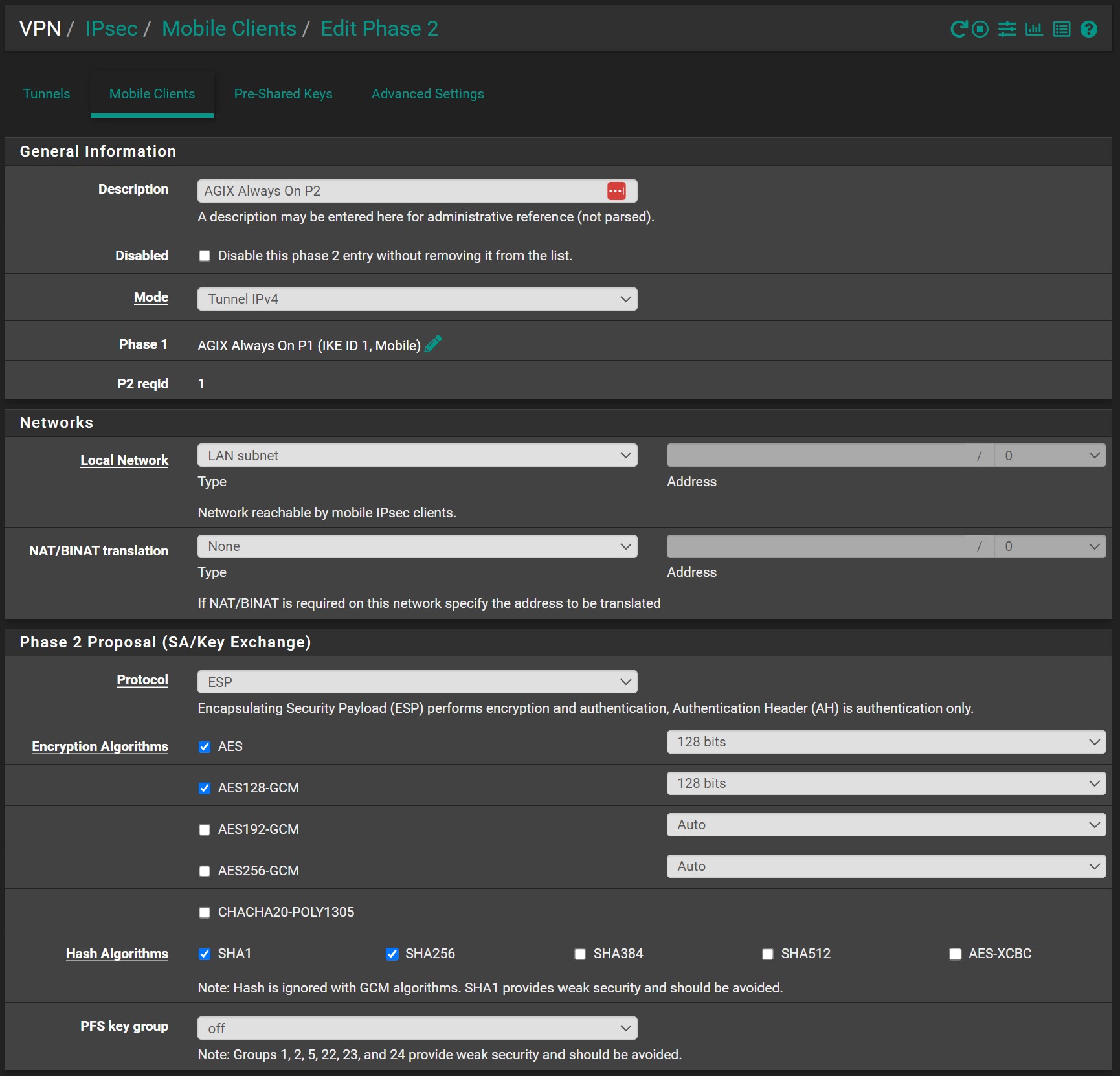
And the Associated Phase 2 (P2):
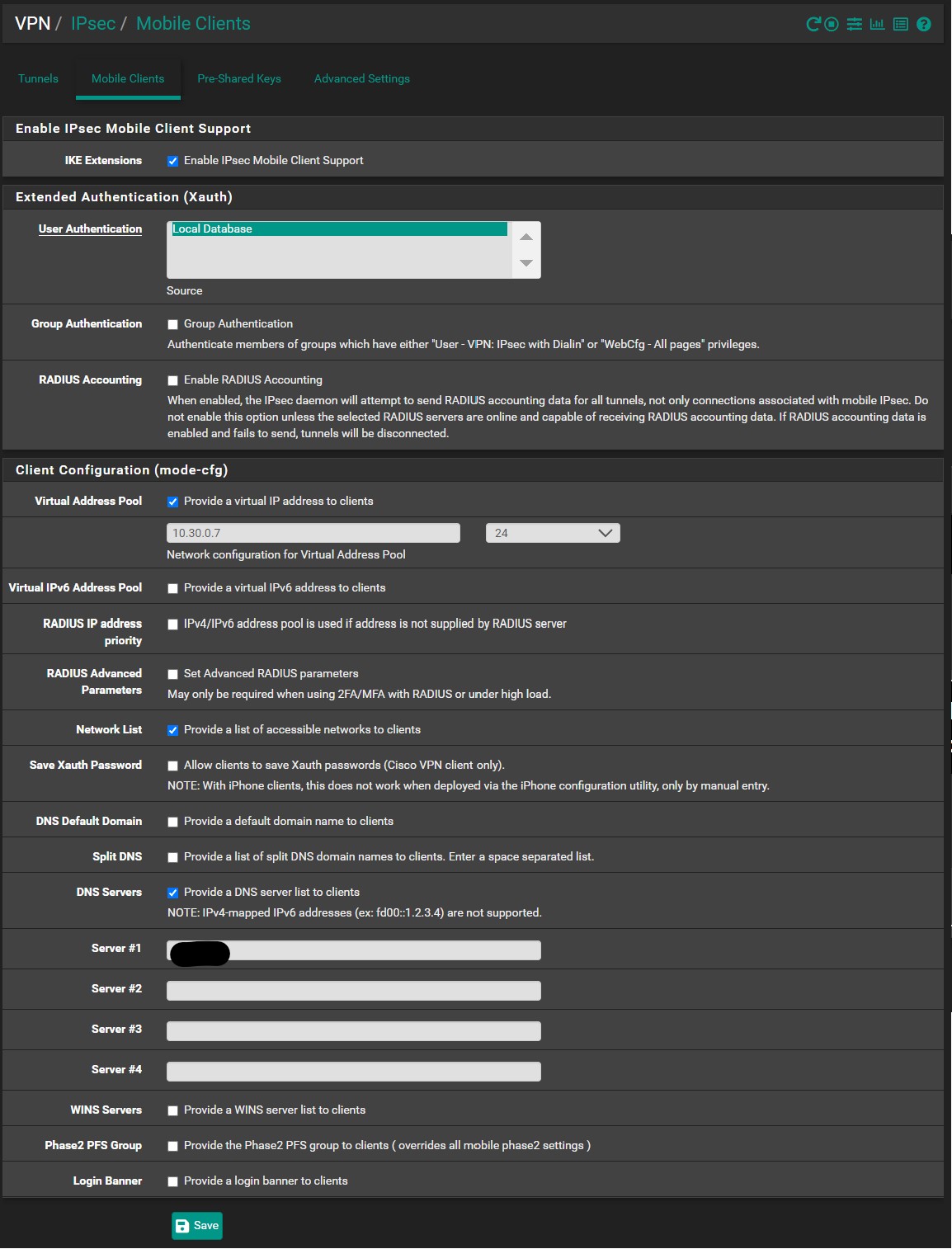
Now to confirm the “Mobile” settings. Change the settings here to meet your needs. The only real changes are the “Virtual Address Pool”, the “Network List” and the “DNS settings”:
We also need a “PSK” (or pre-shared key) for each user. This is the users credentials. The email address and the password as you can see here. The email address will be the username. Why do we have to keep the password in clear text? Because the IPSec process needs to be able to read it for comparison at authentication time. Other options are to use Radius, but we’re not covering that here.
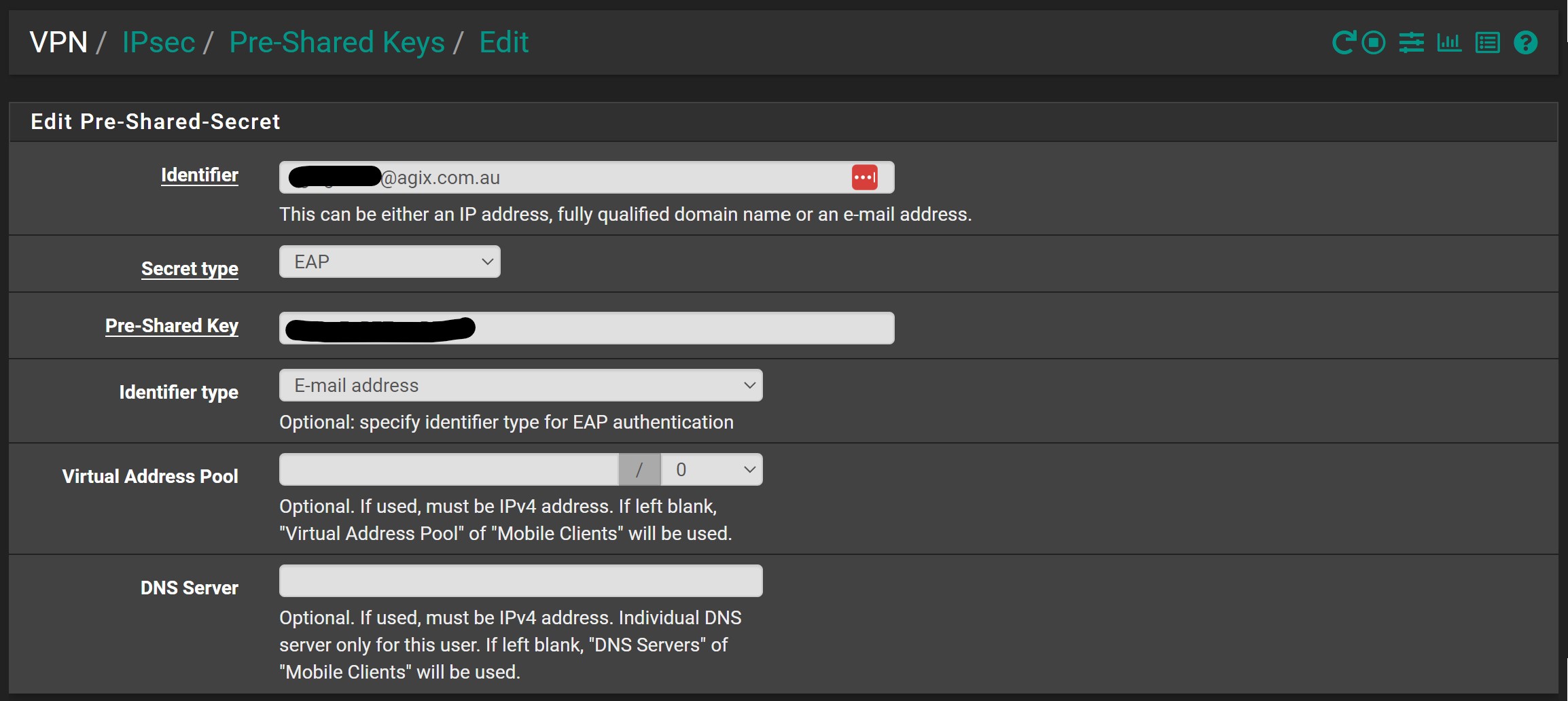
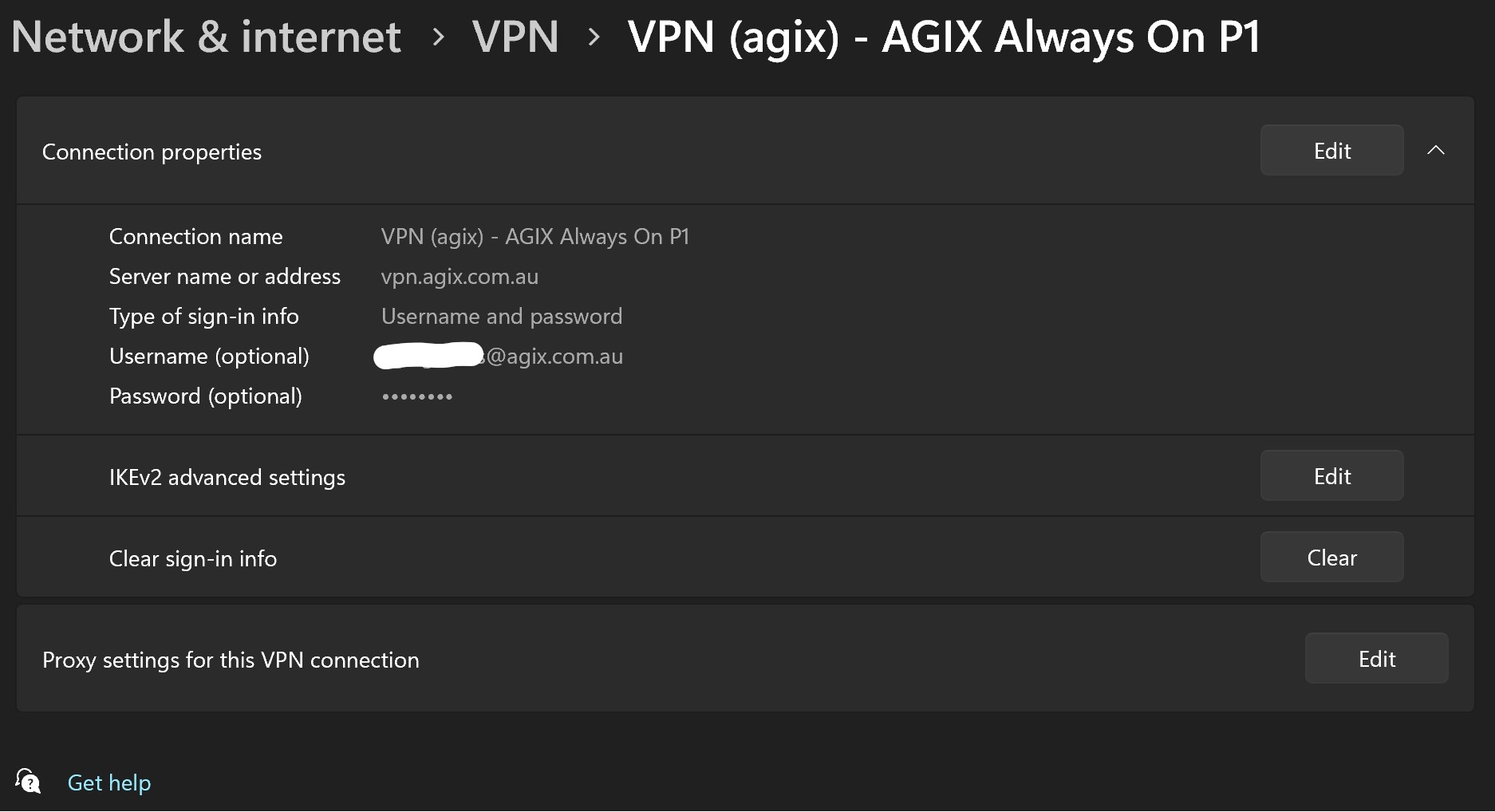
The following is the Windows VPN settings:
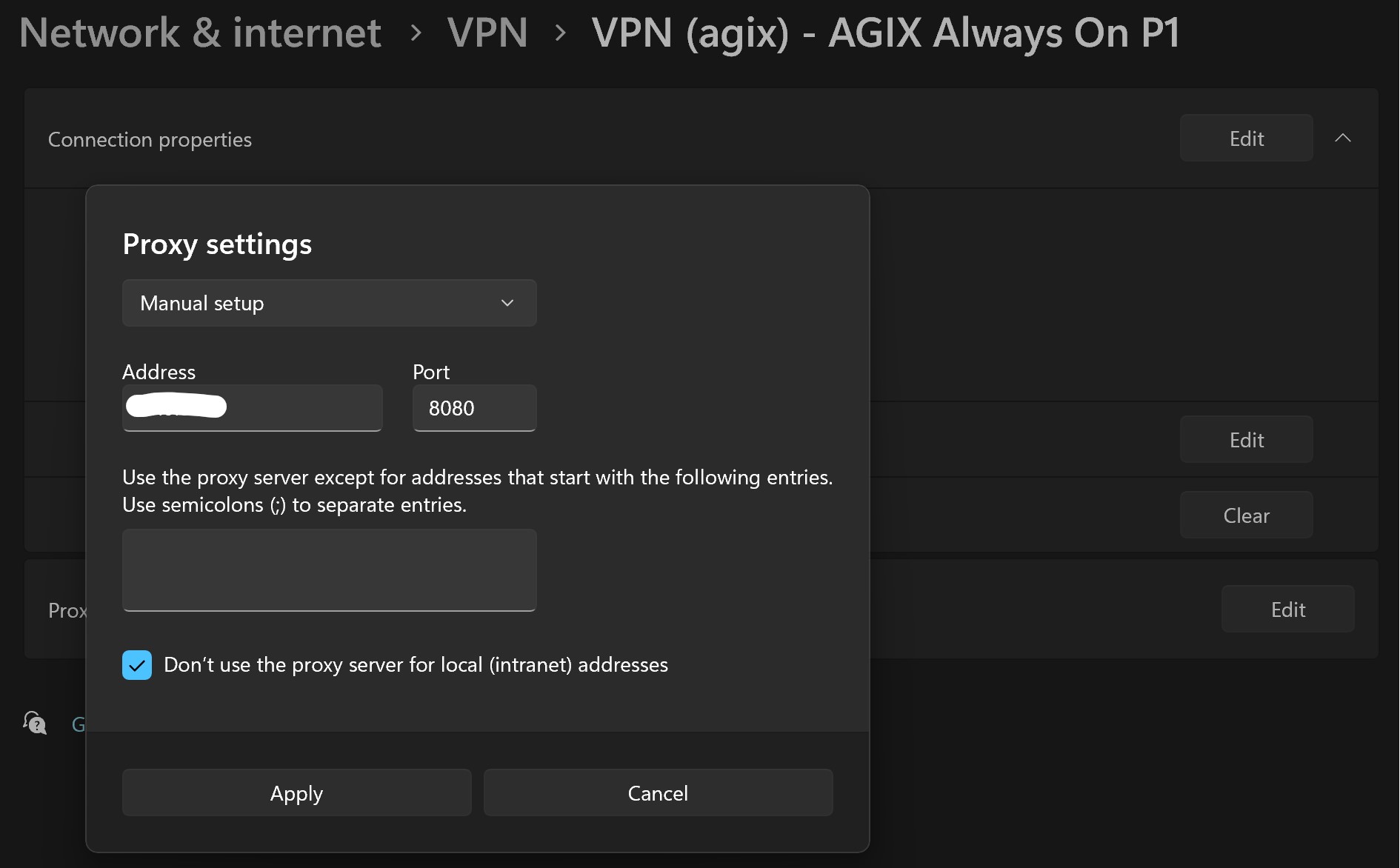
And here’s the optional Proxy settings:
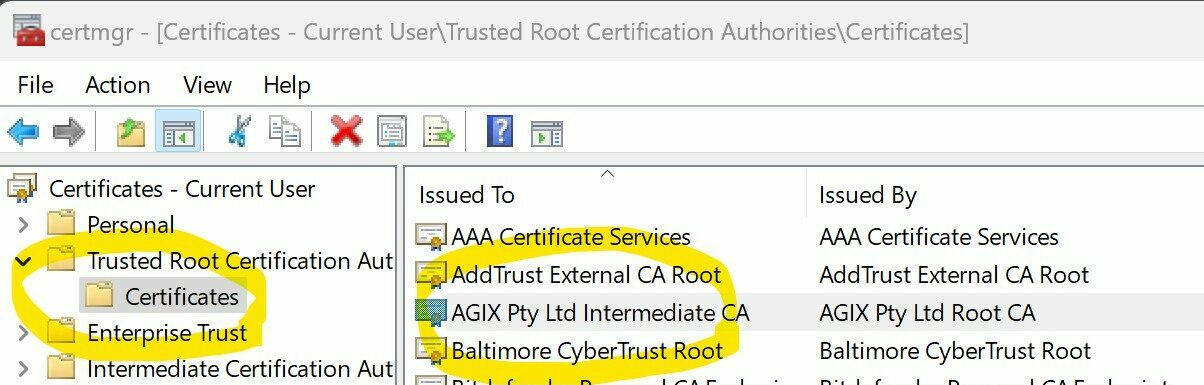
And finally the most important part, the certificate. This is critical to get right. The pfSense CA (if that’s the certificate authority) needs to be trusted by the Windows client. If not, it won’t work.
That should be it. The following shows the status of the VPN from the pfSense point of view. It’s interesting and good that Windows negotiated the stronger encryption protocols (cipher suite).