In this article, we’re assuming we have multiple sites (remote offices) using Unifi networking gear, and a central network (in Azure or AWS for example) running pfSense as the firewall. We want an IPSec site-to-site VPN between them in a spoke topology. The Unifi networks will connect to the pfSense using site-to-site VPNs. There are a few gotchas. The biggest issue is the lack of options within the Unifi console. This is likely because they want you to use Unifi at both ends. But in the real world, that’s unlikely.
Why not use OpenVPN? Because I have no idea how Unifi has implemented it.
We’re focusing on IPSec phase 1. That’s where the NAT issues will be and it matters what IP address you use in your settings. Phase 2 is fully private networking and shouldn’t be your source of pain. In this example, the remote site has a Unifi security gateway connected to a 4G router (that’s not really relevant but helps you get an idea of what we’re working with).
Some networking details:
On the Unifi management portal, go to Devices, USG, Details, WAN 1. Note the IP Address. For me it is “192.168.x.x”. That address is what we enter into the “Local WAN IP” field in the example below. Additionally, we enter the public IP address of the pfSense in the “Peer IP” field.
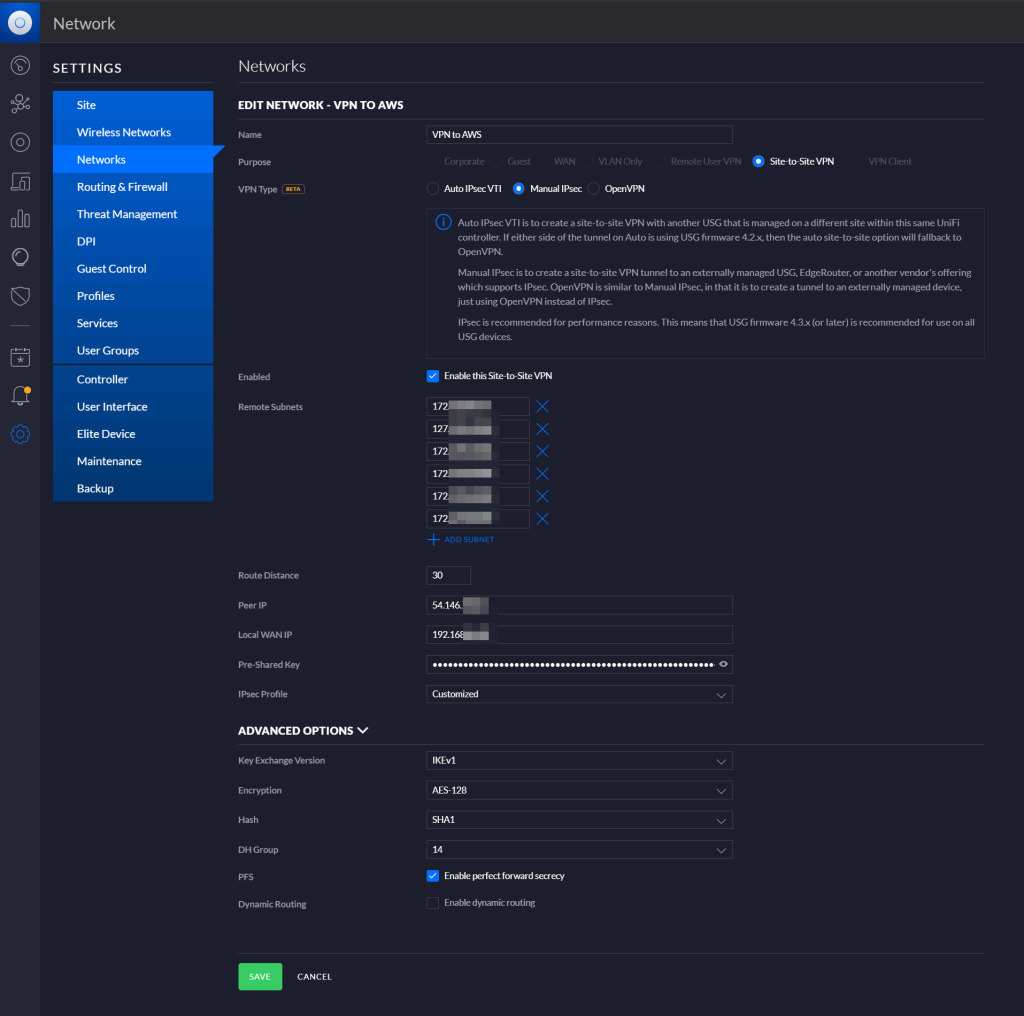
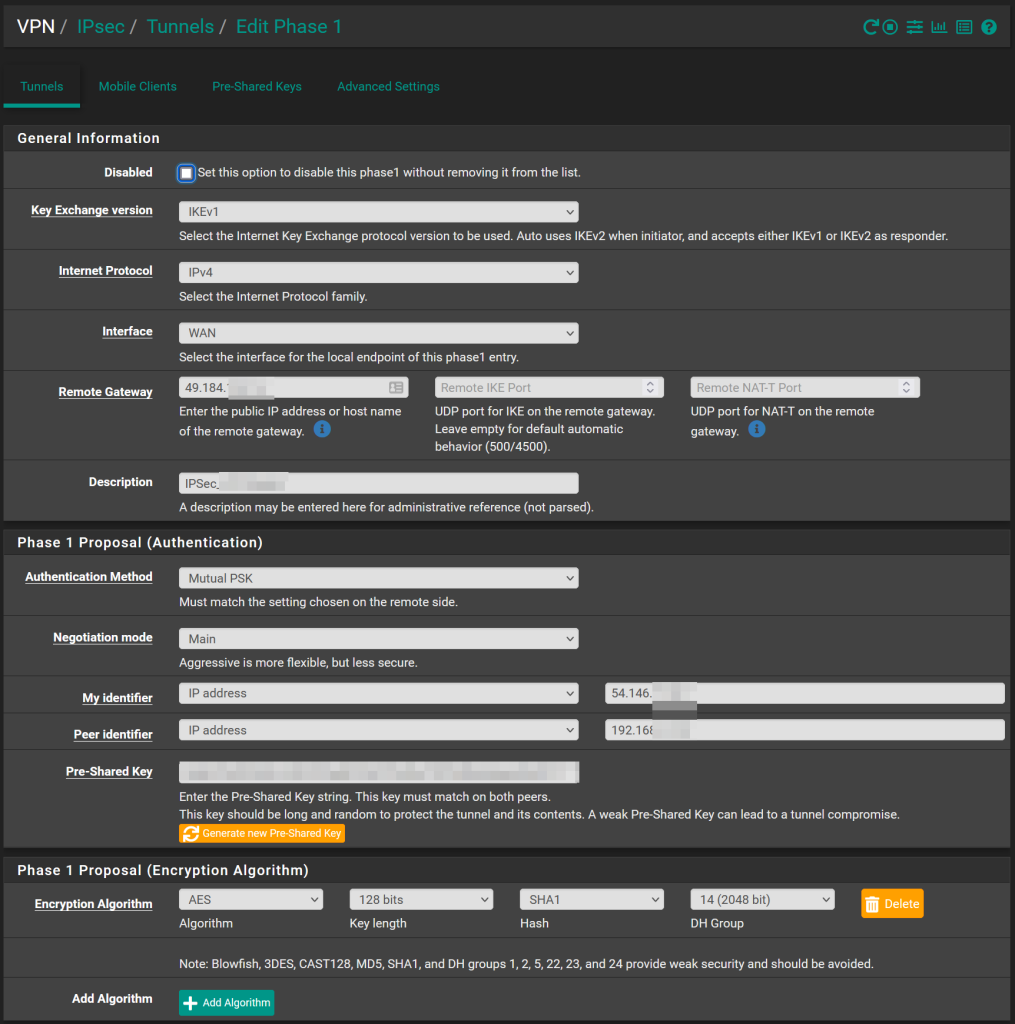
On the pfSense side, we enter the public IP address of the Unifi remote site in the “Remote Gateway” field [1]. Enter the public IP address of the pfSense in the “My identifier” field. And enter the Unifi’s “WAN 1” address (as discussed above) in the “Peer identifier” field. While you’re there, check the crypto settings to make sure your matches. More specifically, make sure your Unifi crypto settings match your pfSense crypto settings. Unfortunately (at this time) you can’t modify anything “time” (re-keying, etc) related on the Unifi side but fortunately the Unifi settings seem to match the pfSense settings well.
Hi,
I have followed your great guide. All the settings seems to be correct but still there is no traffic through the tunnel.
On Pfsense side Phase 1 is established but on USG dashboard site not. What am I doing wrong? Please advice me!
Kind regards,
Matt
Hi Matt,
The issue could be one of several things:
1. Try pining from the USG to the private (inside) IP address of the pfSense to cause some “interesting traffic” to cause the tunnel to come up.
2. If you’re behind NAT on the USG side, make sure the pfSense knows the USG WAN address to use as the identifier.
3. Make sure the Phase 2’s on both ends are correct. Ie, make sure the subnets are correctly specified.
Finally make sure there’s firewall rules on the pfSense to ensure traffic can flow through the tunnel.
I hope this helps.
-Andrew Galdes