Welcome to the second part of the AGIX Cybersecurity training course. This course is focused on staff related matters. Organisationsare under constant attack. Some attacks are “testing the water” while others are organized, local and effective.
Organisations are constantly defending against cyber-threats.
Table of Contents
Targets
- All organisations are targets:
- Online businesses.
- Physical businesses.
- Small businesses.
- Large businesses.
- Not-for-profit.
- Government.
- Defense.
Objectives of criminals
- Financial gain.
- Disruption.
- Intellectual property theft.
- Ransoms.
- Embarrassment.
Methods
- Phishing emails and phone calls:
- Sometimes forged phone numbers.
- Sometimes real phone numbers.
- Invoice payment redirections:
- Forged emails sent to clients with new/fraudulent bank details.
- Fake websites:
- Story about website cloning combined with phishing emails.
- Access to email and social media.
- USB disks:
- Story about “stuxnet”.
- Left around storage devices.
- Hacker tools – Anyone can use them with some Youtube guidance:
- Youtube has thousands (or more) video demonstrations providing guidance for hacking.
- Tools are freely available and downloadable to everyone.
- Ready-to-use Ransomware tools are available for purchase around the $US10 mark.
Exposure points
- Email.
- SMS.
- Social media.
- Phone.
- Mail (post).
- Office (visit).
- Home (visit).
Solutions
- Policies:
- Ensure a suitable and regularly update policy set exists.
- Staff should read and agree to the policies.
- Policies should reflect best practices, but customized to the organisations.
- Working on documents:
- Ensure documents are stored where they’re backed up. Usually a network drive.
- Ensure documents don’t run Macros unless you a confident they’re trustworthy. If not sure, ask.
- Workstation good practices:
- Lock your computer when you leave your chair. (Windows + L).
- Don’t leave laptops in cars or similar locations.
- Don’t plugin USB disks that you don’t trust.
- Report any strange USB devices attached to your computer.
- Verify visitors:
- Site visits are common.
- Assume entrusted before trusted.
- Checks and balances:
- Involve multiple people if unsure/new/suspicious.
- Ensure multiple people are involved in impacting matters.
- Secure physical environments:
- Locked doors.
- Fences.
- Security cameras.
- Guard dogs.
- Security guards.
- Neighbors / Workmates.
- Secure IT environment:
- Ensure that firewalls:
- Block untrusted countries and regions.
- Block inappropriate websites (by domain or content).
- Secure WIFI networks.
- Secure Remote Access systems (VPNs and Remote Desktop).
- Monitor for rogue devices.
- Ensure staff devices:
- Are encrypt (laptops, desktops, phones and tablets).
- Automatically lock after a short period of non-use.
- Are backed up regularly or in real-time.
- Ensure that firewalls:
- USB disks:
- Antivirus should/does scan newly attached storage devices.
- Disks are/should be encrypted when written to, to prevent unauthorized access if lost or stolen.
- Antivirus should/does scan newly attached storage devices.
- Public WIFI:
- It should not be used. Essentially allowing un-trusted computers to communicate.
- Home and Office WIFI:
- Hacker tools are plentiful and can result in your WIFI credentials being stolen. If those credentials match the domain credentials, the hacker has your access.
- Rogue access points (WIFI networks that look like yours/legitimate) allow hackers to steal credentials.
- Procedures need to be followed:
- Finance related departments have high risks of scams and fraudulent requests.
- Generally, policies are designed to protect the business, staff and shareholders.
- Secure online:
- Ensure websites are “https://”.
- Ensure websites are “real”.
- Use a “password manager” and/or your web browsers built-in password manager.
- Set requirements based on risk:
- Require additional checks if thresholds are met or exceeded.
- 2FA:
- If a system allows 2FA, use it.
- It’s very effective.
- Authentication Apps are the best form.
- Email is a less acceptable form.
- SMS is the weakest form.
- Strong passwords:
- Use complex and meaningful passwords.
- Unique passwords:
- Don’t reuse passwords for different systems/services (social media, email, work).
- Incident reporting:
- Can be embarrassing.
- Protect your email accounts at all costs:
- Email is a recovery system.
- Email holds sensitive information.
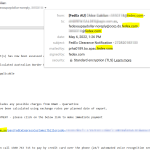
Example Email
The following two images are real emails received. One is a legitimate, while the other is now.


Resources
- https://www.fireeye.com/cyber-map/threat-map.html
- https://haveibeenpwned.com/