Peace of Mind with Robust Linux & Cybersecurity Solutions
Linux & Cybersecurity Solutions: Harden, Audit, Comply
- Achieve Compliance and Secure Your Digital Assets
- Increase Performance and Reliability of your Critical Systems
- Safeguard Your Critical Systems Against Cyber-Attacks


Cybersecurity & Guidance
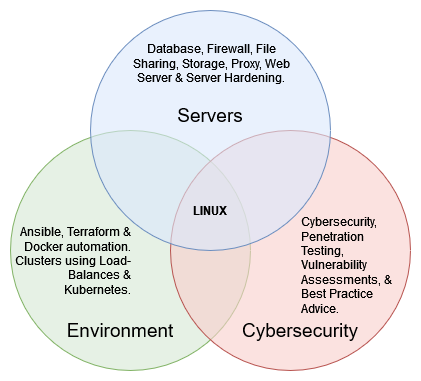
Enhance Your Cybersecurity with AGIX: AGIX understands the critical importance of robust cybersecurity. AGIX recognises the need for advanced server hardening and adherence to best practices and compliance. Many are also required to meet stringent standards such as the Essential 8 and the ISM. AGIX can help.
- Guidance, Gap Analysis & Assessments.
- Penetration Testing & Vulnerability Assessments.
Linux System Administration
Your Linux Support Specialist: AGIX offers comprehensive Linux support tailored to your needs. Whether it's Ubuntu, Redhat, server automation, web, file, or database servers, AGIX's expertise spans a wide range of Linux applications. AGIX is proficient in cloud environments like AWS, understanding their critical role in modern business operations.
- Power your critical work-loads with Linux.
- Automate with Ansible and Terraform.
- Safeguard sensitive data with server hardening.
- Embrace databases clustering for high-availability.

Understanding Our Scope
AGIX is an Adelaide based Australian company with years of experience with Linux, Windows, Networking, Firewalls, Cybersecurity / Information Security, Auditing, Pen-Testing, Framework implementation, Standards implementations, Policy creation and process planning.
AGIX can support your business with Firewalls, Databases, Web Servers, Proxies, File Sharing, DNS, Load-Balancing, System Hardening, Cybersecurity, Frameworks, Standards, Risk Management and so much more.
An Extension of Your Team
When it makes sense to have a Linux team in your IT department, but the funds just aren't there, or the staff turnover is too high, AGIX can fill the gap. AGIX would become a part of your team, responding to tickets just like any other team.
AGIX understand the intricacies of working as part of a remote team. AGIX clients are spread across the world, some have their tech teams in different time-zones, and others don't even have their own staff - everything is outsourced.
Partners
AGIX has partnered with Canonical/Ubuntu, Redhat, Netgate, Lenovo, Ubuntu, BitDefender, VMWare, Veeam, Datto and more to ensure we can supply our clients with everything they need.
By The Book
AGIX is a Pty Ltd company with insurance and various certifications and licenses that combine to show we're trusted and reliable. No corners cut.
AGIX can provide police checks, working with vulnerable people checks, defence checks and more.
Services
AGIX services are focused on business tech support and Cybersecurity. Advice, general support, penetration testing and vulnerability assessments, and resale of hardware and software.
- Linux System Administration
- Cybersecurity Guidance
- Vulnerability Management Programs
- Penetration Testing
- Server Software Support